
Cybersecurity is a vital part of a secure and well-ordered digital world. We are currently living in the Cyber-era, where the internet and computers have a major impact on our way of living and social life. The internet today has gone from being a technical wonder to being a lifestyle imperative. With the expansion of the internet, network security has now become a challenging task. Here comes the role of Cyber-Security. As we morph through Big Data and Industrial Revolution, Cybersecurity keeps us safe from hackers, cyber-criminals, and other agents of fraud.
Cyber-Security protects the data and integrity of computing assets belonging to or connecting to an organization’s network. Its purpose is to defend those assets against all threat actors throughout the entire life cycle of a cyber attack.
Inter IIT Tech Meet 9.0
Inter IIT Tech Meet is an annual technological Competition that was organized by IIT Guwahati this year. The aim is to create a platform that caters to and encourages the continuous need for advancement in technology and human life via new ideas, innovative solutions, and creativity. One of the principal tenets is collaborating with leading government-funded agencies, multinational corporations, and private companies to understand the current problems better. To integrate the collective energy of students for the tempering of Cyber Security, Inter IIT Tech Meet hosted the Network Security Hackathon in collaboration with Saptang Lab.


The participants were provided with various real-world vulnerabilities that have occurred in the past. The motive was to decipher the vulnerabilities by simulating an environment to reproduce the vulnerability exploitation. The challenges presented to the team of participants consisted of CVE numbers (Common Vulnerabilities and Exposures) which the teams worked upon and decoded before setting up an environment to test and develop a PoC (Proof of Concept) exploit. The event involved real-life exploit development for web services like Apache Tomcat, Windows RDP service, and Nginx.
Amongst the fierce competitors, Team IIT Roorkee — Pranav Saxena, Aryaman Behera, Gaurav Genani, Shubhang Tripathi, and Meet Shah bagged the gold medal through their careful analysis and interpretation of the problem. To get a deeper insight into the problem statement, we also approached the team for their valuable perception of modern-day cybersecurity and Network Security.
Conversation with Team IIT Roorkee
1. What are the real-life vulnerabilities mentioned in the problem statement? Why are they significant in Network Security?
To put it in the most basic terms, a computer system vulnerability is a flaw or weakness in a system or network that could be exploited to cause damage or allow an attacker to manipulate the system in some way. These vulnerabilities are not created, rather found by a developer or person using the particular software or application.
Vulnerabilities are always out their in the wild waiting for hackers and developers to exploit it.
The way that a computer vulnerability is exploited depends on the nature of the vulnerability and the attacker's motives. These vulnerabilities can exist because of unanticipated interactions of different software programs, system components, basic flaws in an individual program, hidden backdoor programs, or unknown security bugs. Their significance lies in their difference from a “cyber threat.” A cyber threat may involve an outside element; computer system vulnerabilities exist on the network asset (computer) to begin with. Additionally, they are not usually the result of an intentional effort by an attacker.

2. What do you mean by CVE numbers (Common Vulnerabilities and Exposures)?
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. The MITRE Corporation oversees CVE with funding from the Cybersecurity and Infrastructure Security Agency, part of the U.S. Department of Homeland Security. When someone refers to a CVE, they mean a security flaw that has been assigned a CVE ID number.
CVE is an identification number that is given to every vulnerability and security flaw for easy referencing.
CVE entries are brief. They don’t include technical data or information about risks, impacts, and fixes. Across these different systems, CVE IDs give users a reliable way to tell one unique security flaw from another. CVE must also fulfill a set of criteria, being that they should be independently fixable, acknowledged by the affected vendor, or documented and affecting one codebase.
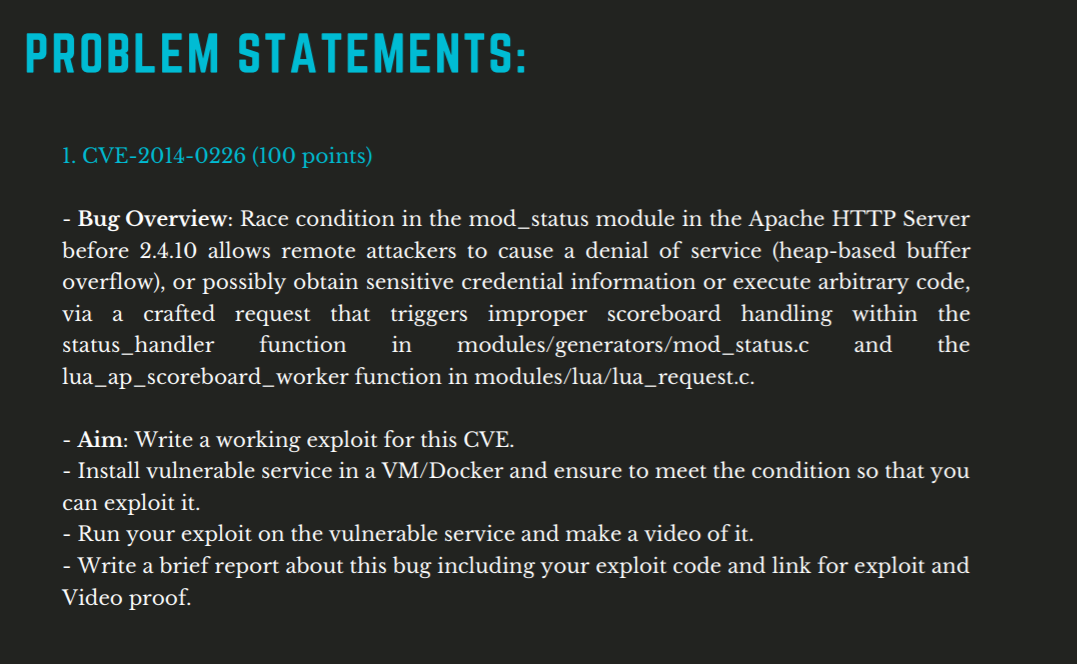
3. What was our approach to this challenge? What are the different steps during the whole course of the hackathon?
- As the CVEs and the related vulnerability had already been rectified, our first step was to find the official public advisory regarding the vulnerability, to identify which types of software and the corresponding version they affected. Then studying the internal workings of the software for a better understanding of the framework. We also read various blogs and articles to get a deeper intuition about how it could be exploited. Therefore, essential time was spent on truly understanding the CVE we wanted to address.
- A differentiating factor for us was finding the vulnerable part of the source code. We used techniques such as source diffing to identify the exact point where the vulnerability was identified and patched. We looked at the code before and after the issue was solved, leaving us with a fairly less code to examine. Since patches are generally small, it is better to determine where exactly the vulnerability exists in their codebase. One could also try to speculate what kind of payload was causing the vulnerability by looking at the checks implemented in the patch.
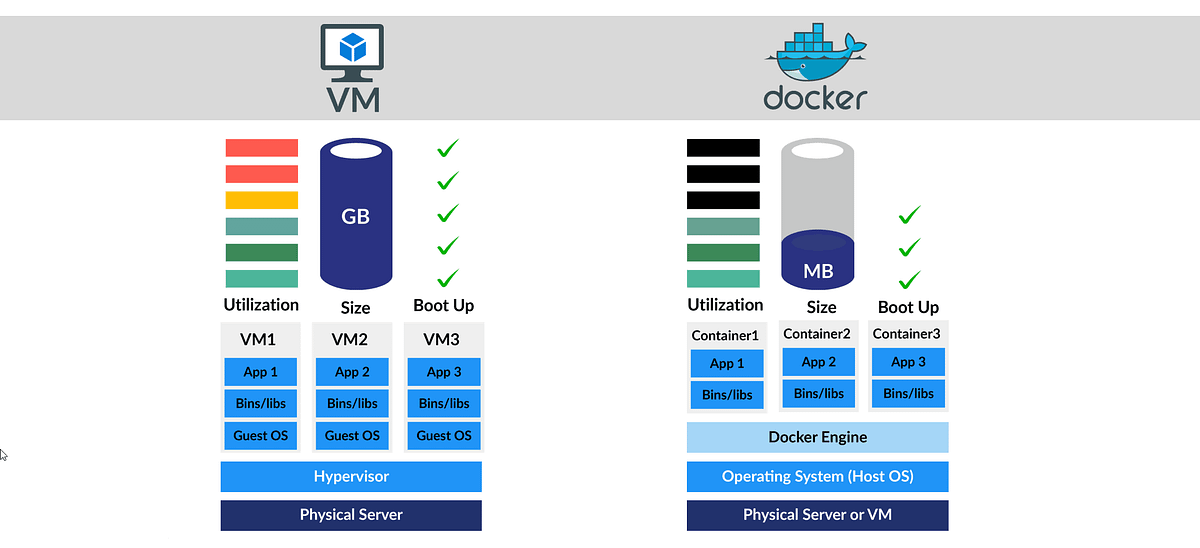
- The next step involves setting up a test environment. A depending factor is knowing which operating system or software version the vulnerability actually occurred. After that, we can deploy our model and simulate the exact environment by creating virtual machines or docker containers for the particular versions. In cases where the vulnerabilities were already patched in the software distribution, we built them from the source at the point when the vulnerability did exist in the codebase.
- Lastly, the actual exploit development consists of figuring out the vulnerability in the environment, crafting payloads for it, and debugging them. This includes a large amount of testing and some trial and error techniques. We also used the practice of escalating our privileges to gain elevated access to resources that are normally protected from an application or user.


4. How did the team coordinate during this online event?
We divided the different problem statements amongst ourselves. Each member started reading about the documentation of the particular CVE number and analyzing the code that caused and affected the vulnerability. In case anybody finished early, they would help others that had a harder CVE to exploit. Most of the communication was done using Discord and using screen sharing to visualize real-time work. Despite the pandemic, our team did our best to perform real-time collaboration and putting the same energy as we would have done in person.
5. What were the major challenges faced by your team during the course of this project?
The major challenges faced by us were:
- For some CVEs, we had to build the vulnerable software from the source itself, which can become quite tedious, especially if it's dependent on old software or a particular version that might lead to compilation errors during the testing phase. These would also include old versions of the dependencies and even the dependencies of their dependencies!
- Some of the vulnerabilities also required the servers to be in a particular configuration apart from being the affected version. These were often not well documented in the CVE, and additional time had to be spent researching around to find the required configuration.
6. What is the significance of this event for the domain of cybersecurity?
One might wonder what more could you get by understanding CVE that have been already addressed or rectified. But it’s these real-life cases that enlighten us about the intricacies of writing bug-free code and understanding the art of identifying exploits in the model.
In a nutshell, the main aim is to get a hands-on learning experience on real-life problems.
Another important reason for studying them is to test if the live version of the software is vulnerable or not. For example, if you want to test 500 Apache servers, you could just run a script 500 times that could actually check them. Therefore these studies can automate a lot of things for the developer.

7. How can someone approach the domain of cybersecurity and explore the different spheres associated? Are there any prerequisites that you need to dive into this field?
At Infosec IITR, we recommend freshers to participate in various CTF (Capture the Flag) events. CTF events are a great way to challenge yourself on problems that are vulnerable by design (i.e., intentionally). You could start your journey by using picoCTF — a well-known hacking contest to help learners of all experience levels. An essential part of participation is to read about the problem carefully and truly understand it before attempting to solve it. We also recommend that you explore CTFtime, which lets you keep track of all the past and upcoming CTFs. An additional feature is that developers can document their versions of solutions to various problems. This could help you get a varied understanding of different approaches and expand your intellect and knowledge. As for the pre-requisites, you should always be curious to learn and explore more. No mathematical experience is needed as such unless you want to work upon cryptography which requires moderate level mathematics. A basic understanding of code could also help you interpret the software or application through a machine’s outlook.
Conclusion
Cybersecurity is an ever-transforming venture continually challenged by hackers, data loss, privacy, risk management, and changing cybersecurity strategies. As the dependency of businesses and companies on cyberspace increases, so do the threats associated with it. Moreover, with the increasing entry points for attacks, more robust cybersecurity is needed to secure networks and devices.
One of the most problematic elements of cybersecurity is the continually evolving nature of security risks. As new technologies emerge and technology is used in new or different ways, new avenues of attack are developed as well. Keeping up with these continual changes and advances in attacks can be challenging for organizations. This also includes ensuring that all the elements of cybersecurity are continually changed and updated to protect against potential vulnerabilities. This is where such competitions like these play their role. As long as the curiosity drives us to explore deeper parts of cybersecurity, we will win against all the threats and challenges and build a digitally safe world.



